On average, cybercrimes are costing US$ 4.24 million to organizations, as per a 2021 report by IBM. It is estimated that cybercrime will cost $10.5 trillion a year by 2025.
Cyber security is the collection of many different practices, techniques, and processes intended to protect computers, networks, programs, data, and devices from theft or damage to the point of possible real catastrophe. It means protecting your IT environment from hackers and other cybercriminals. Cybersecurity is still a major challenge for businesses and organizations in most countries and industries.
What is Cybersecurity?
Cybersecurity is a broad term that represents the protection of information systems and networks from cyber-attacks. Cybersecurity is a multidisciplinary field, combining elements of computer security, law, data security, and privacy. Cybersecurity is such a broad topic that it has spawned its specialized degree programs: Information Systems Security (ISS) and Information Security Management (ISM).
Cybersecurity is focused on safeguarding your information and networks from hackers, viruses, malware, spam, and other malicious attacks. It’s also about protecting your identity against fraud and ensuring that you can safely use the internet.
Just like you lock your car doors when parked on the street or lock your home doors while you’re away at work, cybersecurity practices are necessary to protect valuable information stored on computer systems.
Cybersecurity vs. Computer Security
The terms cybersecurity and computer security are often used interchangeably in everyday language. However, there are some subtle differences between them:
Computer Security – Preventing unauthorized access to data stored on computers or networks through encryption technologies; user authentication; access control; anti-virus software; firewalls; etc.;
Cybersecurity – Protecting information systems from malicious attempts to disrupt operations or steal sensitive data through network defense techniques such as intrusion detection systems; encryption technology; etc.;
Cybersecurity vs. Information Security
The terms cybersecurity and information security are often used interchangeably. Cybersecurity is the collective effort taken to protect networks, devices, applications, and data from attack and damage. Information security builds on that foundation to address data in all forms, whether analog or digital. Cybersecurity professionals deal with cybercrimes, cyber attacks, and cyberwar. Information security professionals deal with protection from unauthorized access, disclosure, alteration, or destruction of data.

Why Is Cybersecurity Important?
In light of the sheer number of digital platforms and highly sensitive data used in today’s online world, security for cyber activity has become increasingly important.
“On average, cybercrimes are costing US$ 4.24 million to organizations, as per a 2021 report by IBM. It is estimated that cybercrime will cost $10.5 trillion a year by 2025.”
Cyber attacks cost companies billions every year in lost productivity, damaged reputations, and lawsuits. Paloalto blog reports that according to IBM and the Ponemon Institute’s 2020 “Cost of a Data Breach” report, it was determined that the average total cost of cybersecurity breaches in the United States of America, between August 2019 and April 2020, was $8,640,000. Cyber incidents are no longer a far-fetched concept within the realm of what could go wrong. The consensus among industry experts is that an organization facing a cybersecurity breach or attack is not a matter of “if,” but rather “when.” Even seemingly “minor” cybersecurity incidents can have devastating effects on the financial, reputational, and operational success of an enterprise.
The following are a few reasons why cybersecurity is so important.
- The costs of cyber security breaches are rising
Privacy laws such as the GDPR (General Data Protection Regulation) and DPA (Data Protection Act) 2018 can mean significant fines for organizations that suffer cyber security breaches. There are also non-financial costs to be considered, like reputational damage.
- Cyber attacks are increasingly sophisticated
Cyber-attacks continue to grow in sophistication, with attackers using an ever-expanding variety of tactics. These include social engineering, malware, and ransomware.
- Cyber security is a critical, board-level issue
New regulations and reporting requirements make cyber security risk oversight a challenge. The board needs assurance from management that its cyber risk strategies will reduce the risk of attacks and limit financial and operational impacts.
- Cybercrime is a big business
According to The hidden costs of cybercrime, a 2020 study carried out by McAfee and the CSIS (Centre for Strategic and International Studies), based on data collected by Vanson Bourne, the world economy loses more than $1 trillion (approximately £750 billion) each year. Political, ethical, and social incentives can also drive attackers.
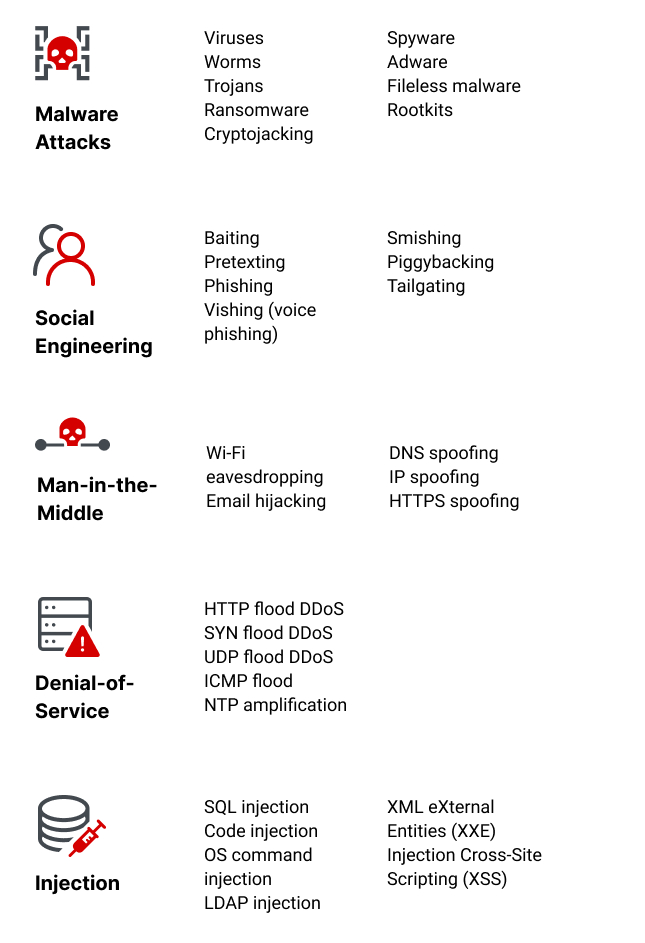
Types of Cybersecurity Threats and Attacks
Cybersecurity threats are acts committed with malicious intent to steal data, and cause damage to or disrupt computing systems. Threats are often categorized by the type of attack they use. These types include malware, social engineering, man-in-the-middle (MitM) attacks, denial of service (DoS), and injection attacks. The perpetrators of cyber attacks can be divided into several different categories. These include nation-states or terrorist groups, as well as individual hackers and even trusted individuals who abuse their privileges to commit malicious acts.
Common Sources of Cyber Threats
- Nation-states – hostile countries can launch cyberattacks against local companies and institutions, aiming to interfere with communications, cause disorder, and inflict damage.
- Terrorist organizations – terrorists conduct cyber attacks aimed at destroying or abusing critical infrastructure, threatening national security, disrupting economies, and causing bodily harm to citizens.
- Criminal groups – organized groups of hackers who aim to break into computing systems for economic benefit. These groups use phishing, spam, spyware, and malware for extortion, theft of private information, and online scams.
- Hackers – individual hackers target organizations using a variety of attack techniques. They are usually motivated by personal gain, revenge, financial gain, or political activity. Hackers often develop new threats, to advance their criminal ability and improve their standing in the hacker community.
- Malicious insiders – an employee who has legitimate access to company assets, and abuses their privileges to steal information or damage computing systems for economic or personal gain. Insiders may be employees, contractors, suppliers, or partners of the target organization. They can also be outsiders who have compromised a privileged account and are impersonating its owner.
Types of Cybersecurity Threats
Malware Attacks
Malware is an abbreviation of “malicious software”, which includes viruses, worms, trojans, spyware, and ransomware, and is the most common type of cyberattack. Malware infiltrates a system, usually via a link on an untrusted website or email or any unwanted software download. It deploys on the target system, collects sensitive data, manipulates and blocks access to network components, and may destroy data or shut down the system altogether.
Here are some of the main types of malware attacks:
- Viruses—a piece of code that injects itself into an application. When the application runs, the malicious code executes.
- Worms—malware that exploits software vulnerabilities and backdoors to gain access to an operating system. Once installed in the network, the worm can carry out attacks such as distributed denial of service (DDoS).
- Trojans—malicious code or software that poses as an innocent program, hiding in apps, games, or email attachments. An unsuspecting user downloads the trojan, allowing it to gain control of its device.
- Ransomware—a user or organization is denied access to their systems or data via encryption. The attacker typically demands a ransom be paid in exchange for a decryption key to restore access, but no guarantee paying the ransom will restore full access or functionality.
- Cryptojacking—attackers deploy software on a victim’s device, and begin using their computing resources to generate cryptocurrency, without their knowledge. Affected systems can become slow and cryptojacking kits can affect system stability.
- Spyware—a malicious actor gains access to an unsuspecting user’s data, including sensitive information such as passwords and payment details. Spyware can affect desktop browsers, mobile phones, and desktop applications.
- Adware—a user’s browsing activity is tracked to determine behavior patterns and interests, allowing advertisers to send the user-targeted advertising. Adware is related to spyware but does not involve installing software on the user’s device and is not necessarily used for malicious purposes, but it can be used without the user’s consent and compromise their privacy.
- Fileless malware—no software is installed on the operating system. Native files like WMI and PowerShell are edited to enable malicious functions. This stealthy form of attack is difficult to detect (antivirus can’t identify it), because the compromised files are recognized as legitimate.
- Rootkits—software is injected into applications, firmware, operating system kernels, or hypervisors, providing remote administrative access to a computer. The attacker can start the operating system within a compromised environment, gain complete control of the computer and deliver additional malware.
Social Engineering Attacks
Social engineering involves tricking users into providing an entry point for malware. The victim provides sensitive information or unwittingly installs malware on their device because the attacker poses as a legitimate actor.
Here are some of the main types of social engineering attacks:
- Baiting—the attacker lures a user into a social engineering trap, usually with a promise of something attractive like a gift card. The victim provides sensitive information such as credentials to the attacker.
- Pretexting—similar to baiting, the attacker pressures the target into giving up information under pretenses. This typically involves impersonating someone with authority, for example, an IRS or police officer, whose position will compel the victim to comply.
- Phishing—the attacker sends emails pretending to come from a trusted source. Phishing often involves sending fraudulent emails to as many users as possible, but can also be more targeted. For example, “spear phishing” personalizes the email to target a specific user, while “whaling” takes this a step further by targeting high-value individuals such as CEOs.
- Vishing (voice phishing)—the imposter uses the phone to trick the target into disclosing sensitive data or grant access to the target system. Vishing typically targets older individuals but can be employed against anyone.
- Smishing (SMS phishing)—the attacker uses text messages as a means of deceiving the victim.
- Piggybacking—an authorized user provides physical access to another individual who “piggybacks” off the user’s credentials. For example, an employee may grant access to someone posing as a new employee who misplaced their credential card.
- Tailgating—an unauthorized individual follows an authorized user into a location, for example by quickly slipping in through a protected door after the authorized user has opened it. This technique is similar to piggybacking except that the person being tailgated is unaware that they are being used by another individual.
Supply Chain Attacks
Supply chain attacks are a new type of threat to software developers and vendors. Its purpose is to infect legitimate applications and distribute malware via source code, build processes, or software update mechanisms.
Attackers are looking for non-secure network protocols, server infrastructure, and coding techniques, and use them to compromise the build and update process, modify source code and hide malicious content.
Supply chain attacks are especially severe because the applications being compromised by attackers are signed and certified by trusted vendors. In a software supply chain attack, the software vendor is not aware that its applications or updates are infected with malware. Malicious code runs with the same trust and privileges as the compromised application.
Types of supply chain attacks include:
- Compromise of build tools or development pipelines
- Compromise of code signing procedures or developer accounts
- Malicious code sent as automated updates to hardware or firmware components
- Malicious code pre-installed on physical devices
Man-in-the-Middle Attack
A Man-in-the-Middle (MitM) attack involves intercepting the communication between two endpoints, such as a user and an application. The attacker can eavesdrop on the communication, steal sensitive data, and impersonate each party participating in the communication.
Examples of MitM attacks include:
- Wi-Fi eavesdropping—an attacker sets up a Wi-Fi connection, posing as a legitimate actor, such as a business, that users may connect to. The fraudulent Wi-Fi allows the attacker to monitor the activity of connected users and intercept data such as payment card details and login credentials.
- Email hijacking—an attacker spoofs the email address of a legitimate organization, such as a bank, and uses it to trick users into giving up sensitive information or transferring money to the attacker. The user follows instructions they think come from the bank but are actually from the attacker.
- DNS spoofing—a Domain Name Server (DNS) is spoofed, directing a user to a malicious website posing as a legitimate site. The attacker may divert traffic from the legitimate site or steal the user’s credentials.
- IP spoofing—an internet protocol (IP) address that connects users to a specific website. An attacker can spoof an IP address to pose as a website and deceive users into thinking they are interacting with that website.
- HTTPS spoofing—HTTPS is generally considered the more secure version of HTTP, but can also be used to trick the browser into thinking that a malicious website is safe. The attacker uses “HTTPS” in the URL to conceal the malicious nature of the website.
Denial-of-Service Attack
A Denial-of-Service (DoS) attack overloads the target system with a large volume of traffic, hindering the ability of the system to function normally. An attack involving multiple devices is known as a distributed denial-of-service (DDoS) attack.
DoS attack techniques include:
- HTTP flood DDoS—the attacker uses HTTP requests that appear legitimate to overwhelm an application or web server. This technique does not require high bandwidth or malformed packets and typically tries to force a target system to allocate as many resources as possible for each request.
- SYN flood DDoS—initiating a Transmission Control Protocol (TCP) connection sequence involves sending an SYN request that the host must respond to with an SYN-ACK that acknowledges the request, and then the requester must respond with an ACK. Attackers can exploit this sequence, tying up server resources, by sending SYN requests but not responding to the SYN-ACKs from the host.
- UDP flood DDoS—a remote host is flooded with User Datagram Protocol (UDP) packets sent to random ports. This technique forces the host to search for applications on the affected ports and respond with “Destination Unreachable” packets, which use up the host resources.
- ICMP flood—a barrage of ICMP Echo Request packets overwhelms the target, consuming both inbound and outgoing bandwidth. The servers may try to respond to each request with an ICMP Echo Reply packet, but cannot keep up with the rate of requests, so the system slows down.
- NTP amplification—Network Time Protocol (NTP) servers are accessible to the public and can be exploited by an attacker to send large volumes of UDP traffic to a targeted server. This is considered an amplification attack due to the query-to-response ratio of 1:20 to 1:200, which allows an attacker to exploit open NTP servers to execute high-volume, high-bandwidth DDoS attacks.
Injection Attacks
Injection attacks exploit a variety of vulnerabilities to directly insert malicious input into the code of a web application. Successful attacks may expose sensitive information, execute a DoS attack or compromise the entire system.
Here are some of the main vectors for injection attacks:
- SQL injection—an attacker enters an SQL query into an end-user input channel, such as a web form or comment field. A vulnerable application will send the attacker’s data to the database and will execute any SQL commands that have been injected into the query. Most web applications use databases based on Structured Query Language (SQL), making them vulnerable to SQL injection. A new variant of this attack is NoSQL attacks, which targeted databases that do not use a relational data structure.
- Code injection—an attacker can inject code into an application if it is vulnerable. The webserver executes the malicious code as if it were part of the application.
- OS command injection—an attacker can exploit a command injection vulnerability to input commands for the operating system to execute. This allows the attack to exfiltrate OS data or take over the system.
- LDAP injection—an attacker inputs characters to alter Lightweight Directory Access Protocol (LDAP) queries. A system is vulnerable if it uses unsanitized LDAP queries. These attacks are very severe because LDAP servers may store user accounts and credentials for an entire organization.
- XML eXternal Entities (XXE) Injection—an attack is carried out using specially-constructed XML documents. This differs from other attack vectors because it exploits inherent vulnerabilities in legacy XML parsers rather than unvalidated user inputs. XML documents can be used to traverse paths, execute code remotely and execute server-side request forgery (SSRF).
- Cross-Site Scripting (XSS)—an attacker inputs a string of text containing malicious JavaScript. The target’s browser executes the code, enabling the attacker to redirect users to a malicious website or steal session cookies to hijack a user’s session. An application is vulnerable to XSS if it doesn’t sanitize user inputs to remove JavaScript code.
Common Questions about Cybersecurity Threats
what is phishing in Cybersecurity?
Phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity. Phishing messages manipulate a user, causing them to perform actions like installing a malicious file, clicking a malicious link, or divulging sensitive information such as access credentials. Phishing is the most common type of social engineering, which is a general term describing attempts to manipulate or trick computer users.
what is spear phishing in Cybersecurity?
Spear phishing is an email or electronic communications scam targeted toward a specific individual, organization, or business. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
what is whaling in Cybersecurity?
A whaling attack is a method used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization, to steal money or sensitive information or gain access to their computer systems for criminal purposes. Also known as CEO fraud, whaling is similar to phishing in that it uses methods such as email and website spoofing to trick a target into performing specific actions, such as revealing sensitive data or transferring money. Read More here.
what is tailgating in Cybersecurity?
Tailgating is a simple social engineering attack enabling hackers to gain access to a password-protected or otherwise off-limits physical location. Tailgating involves closely following an authorized person into a restricted access area. As a regular employee opens a heavy door, for example, a tailgating social engineer may grab the door as it’s about to close, waling right into the targeted physical system.
Direct tailgating attempts do not work in all environments. Established organizations commonly have entry-oriented security protocols in place; from biometrics-based systems, to badge systems, to other forms of identification. Nonetheless, it may be possible for a bad actor to start chatting with employees, and to leverage this type of familiarity to get into otherwise secured areas. Attackers will attempt to pressure or otherwise psychologically manipulate potential unwitting tailgating attack ‘accomplices’.
Tailgating attacks vs. Piggybacking
The tailgating attack definition can also include another type of social engineering; known as piggybacking. In these types of attacks, attackers also gain entry into a restricted area without authorization. In Piggybacking attack situations, however, persons with access permissions are aware of providing unauthorized entry to someone else.
What is a Zero-day Attack?
“Zero-day” is a broad term that describes recently discovered security vulnerabilities that hackers can use to attack systems. The term “zero-day” refers to the fact that the vendor or developer has only just learned of the flaw – which means they have “zero days” to fix it. A zero-day attack takes place when hackers exploit the flaw before developers have a chance to address it.
Zero-day is sometimes written as 0-day. The words vulnerability, exploit, and attack are typically used alongside zero-day, and it’s helpful to understand the difference:
- A zero-day vulnerability is a software vulnerability discovered by attackers before the vendor has become aware of it. Because the vendors are unaware, no patch exists for zero-day vulnerabilities, making attacks likely to succeed.
- A zero-day exploit is a method hackers use to attack systems with a previously unidentified vulnerability.
- A zero-day attack is the use of a zero-day exploit to cause damage to or steal data from a system affected by a vulnerability.
Software often has security vulnerabilities that hackers can exploit to cause havoc. Software developers are always looking out for vulnerabilities to “patch” – that is, develop a solution that they release in a new update.
However, sometimes hackers or malicious actors spot the vulnerability before the software developers do. While the vulnerability is still open, attackers can write and implement a code to take advantage of it. This is known as exploit code.
The exploit code may lead to the software users being victimized – for example, through identity theft or other forms of cybercrime. Once attackers identify a zero-day vulnerability, they need a way of reaching the vulnerable system. They often do this through a socially engineered email – i.e., an email or other message that is supposedly from a known or legitimate correspondent but is actually from an attacker. The message tries to convince a user to act by opening a file or visiting a malicious website. Doing so downloads the attacker’s malware, which infiltrates the user’s files and steals confidential data. Read More Here
What is a cybersecurity breach?
A security breach is any incident that results in unauthorized access to computer data, applications, networks, or devices. It results in information being accessed without authorization. Typically, it occurs when an intruder can bypass security mechanisms.
Technically, there’s a distinction between a security breach and a data breach. A security breach is effectively a break-in, whereas a data breach is defined as a cybercriminal getting away with information. Imagine a burglar; the security breach is when he climbs through the window, and the data breach is when he grabs your pocketbook or laptop and takes it away.
Confidential information has immense value. It’s often sold on the dark web; for example, names and credit card numbers can be bought, and then used for identity theft or fraud. It’s not surprising that security breaches can cost companies huge amounts of money. On average, the bill is nearly $4m for major corporations.
What is a cybersecurity Crime?
Cybercrime is defined as an unlawful action against any person using a computer, its systems, and its online or offline applications. It occurs when information technology is used to commit or cover an offense. However, the act is only considered Cybercrime if it is intentional and not accidental.
Dangerous cybersecurity myths
The volume of cybersecurity incidents is on the rise across the globe, but misconceptions continue to persist, including the notion that:
- Cybercriminals are outsiders. In reality, cybersecurity breaches are often the result of malicious insiders, working for themselves or in concert with outside hackers. These insiders can be a part of well-organized groups, backed by nation-states.
- Risks are well-known. The risk surface is still expanding, with thousands of new vulnerabilities being reported in old and new applications and devices. And opportunities for human error – specifically by negligent employees or contractors who unintentionally cause a data breach – keep increasing.
- Attack vectors are contained. Cybercriminals are finding new attack vectors all the time – including Linux systems, operational technology (OT), Internet of Things (IoT) devices, and cloud environments.
- My industry is safe. Every industry has its share of cybersecurity risks, with cyber adversaries exploiting the necessities of communication networks within almost every government and private-sector organization. For example, ransomware attacks (see below) are targeting more sectors than ever, including local governments and non-profits, and threats on supply chains, “.gov” websites, and critical infrastructure have also increased.
What are the Cybersecurity Best Practices?
Cyberattacks and cybercrimes are alarming. Large and small companies alike suffer data breaches, and hackers increasingly target smaller businesses, knowing that their defenses might be less robust. The cybersecurity firm BullGuard estimates that roughly 43 percent of small businesses have no cybersecurity defense plan. As remote working grew more frequent during the pandemic, these risks became even greater.
%
*roughly 43% of small businesses have no cybersecurity defense plan
There are several basic common sense cybersecurity techniques that businesses and individuals can use to protect themselves.
Raise cybersecurity awareness
The first piece of advice is actually about your ability to build effective communication with all of your employees as well as to educate them on possible cybersecurity threats and ways to mitigate them.
Employ a people-centric security approach
People can be your biggest security risk or your strongest security defense.
Nowadays, a technology-centric approach to cybersecurity isn’t enough to ensure all-around protection because hackers often use people as an entry point. That’s why it’s best to use a people-centric approach for mitigating human-connected risks.
In people-centric security, an important perimeter is the workers themselves. Organizations give employees the autonomy to adopt security measures, handle information, and use devices by:
- Trusting them
- Making them responsible for the security of the corporate data they use
Still, you need to ensure all of your employees follow the cybersecurity practices recommended by your security policy.
Reduce the level of employee negligence
%
* 62% of all insider data breaches were caused by employee errors
Last year, 62% of all insider data breaches were caused by employee errors or negligence according to the 2022 Ponemon Cost of Insider Threats Global Report.
- Raise awareness of cyber threats your company faces and how they affect the bottom line.
- Explain to your employees the importance of each computer security measure (installing only trusted applications, protecting endpoints against malware).
- Show examples of real-life security breaches, their consequences, and the difficulty of the recovery process.
- Ask employees for feedback regarding the current corporate security system (how to combine robust security with an efficient workflow).
As an example, you can look at information about steps for employee engagement and training on the UK National Cyber Security Centre page. Additionally, you can find the UK government’s new cyber security business guidance here. Please note that requirements and recommendations may differ across countries and regions.
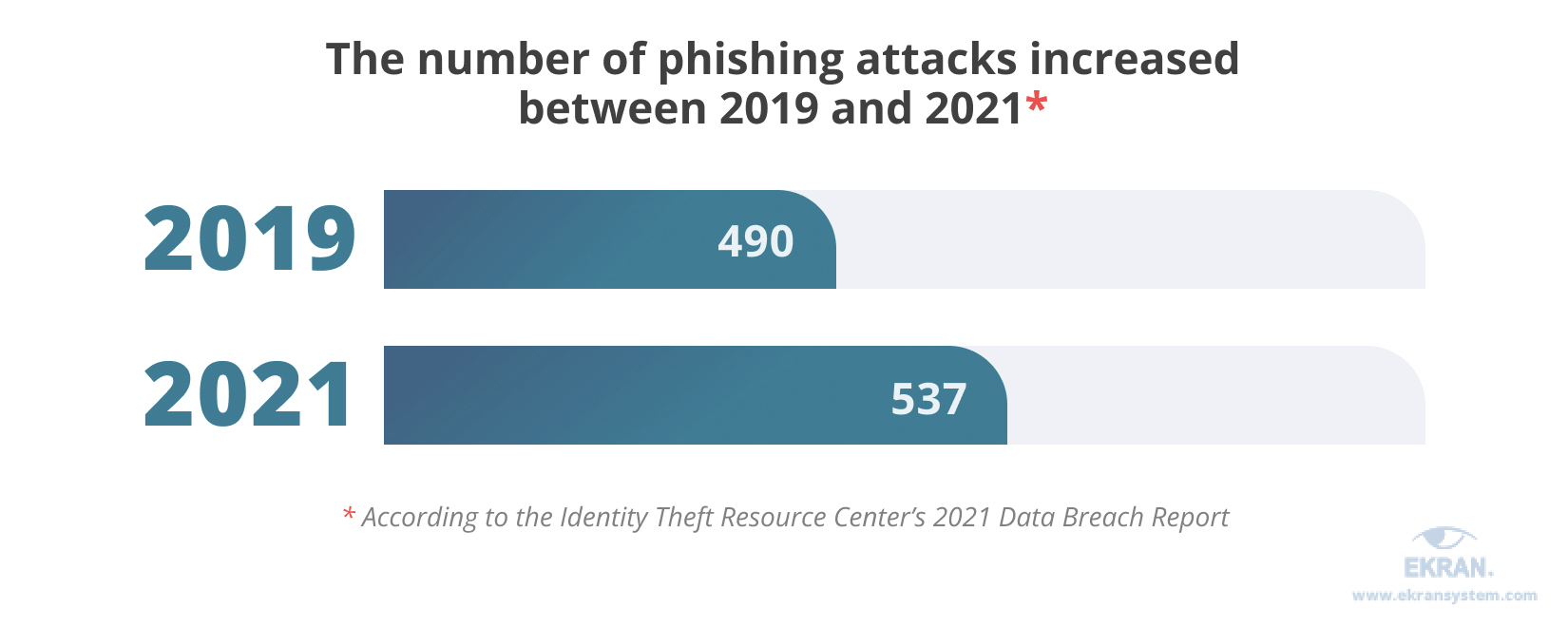
Inform employees about common phishing techniques
Cyber attackers often use phishing techniques to obtain employees’ credentials and infect an organization’s systems with malware, or acquire employees’ financial information.
Protect access to your critical assets
Protect access from remote devices
Ensure access management for any type of user.
Securing access to your sensitive data from any location and device is critical. Remote workers, as well as employees using their own devices, play a more significant role in an organization’s security today than ever before.
According to the 2021 BYOD Security Report by Bitglass [PDF], 82% of 271 organizations surveyed in April 2021 have actively adopted a Bring Your Device (BYOD) approach. Meanwhile, security concerns are among the top barriers to BYOD adoption.

Handle passwords securely
Privileged accounts are gems for cybercriminals who attempt to gain access to your sensitive data and valuable business information. Password management is a key part of corporate security, especially when it comes to privileged access management (PAM).
The largest online leak of emails and passwords ever happened in 2021: the Compilation of Many Breaches, an online hacking forum, posted 3.27 billion credential pairs. This open database includes passwords from many past leaks of LinkedIn, Netflix, Bitcoin, and Exploit.in, Yahoo, Gmail, Hotmail, and other services. The Compilation of Many Breaches indicates the importance of password management and changing passwords regularly.
The best way to ensure proper security is to use specialized tools, such as password vaults and PAM solutions. This way, you can prevent unauthorized users from accessing privileged accounts and simplify password management for employees at the same time.
- Use one password for one account.
- Use memorable phrases instead of short strings of random characters.
- Use mnemonics or other tactics to remember long passwords.
- Don’t share credentials, no matter how convenient it is.
- Change passwords after a set period.
The National Cybersecurity and Communications Integration Center have created a set of cybersecurity recommendations for choosing and protecting strong passwords.
Use the principle of least privilege
Granting new employees all privileges by default allows them to access sensitive data even if they don’t need to. Such an approach increases the risk of insider threats and allows hackers access to sensitive data as soon as a single employee account is compromised.
Privilege abuse is the leading cause of data breaches according to the 2021 Data Breach Investigations Report by Verizon.
A much better solution is to use the principle of least privilege (POLP).
Protect your data
Keep an eye on privileged users
Privileged users have all the means necessary to steal your sensitive data and go unnoticed. Even if you trust your users and they don’t intend to act maliciously, their actions can unintentionally cause a leak, or hackers can break into their accounts.
It’s not surprising that many organizations monitor privileged accounts more closely than other accounts (61% of organizations surveyed), applications, devices, and documents according to the 2021 Insider Threat Report by Cybersecurity Insiders.
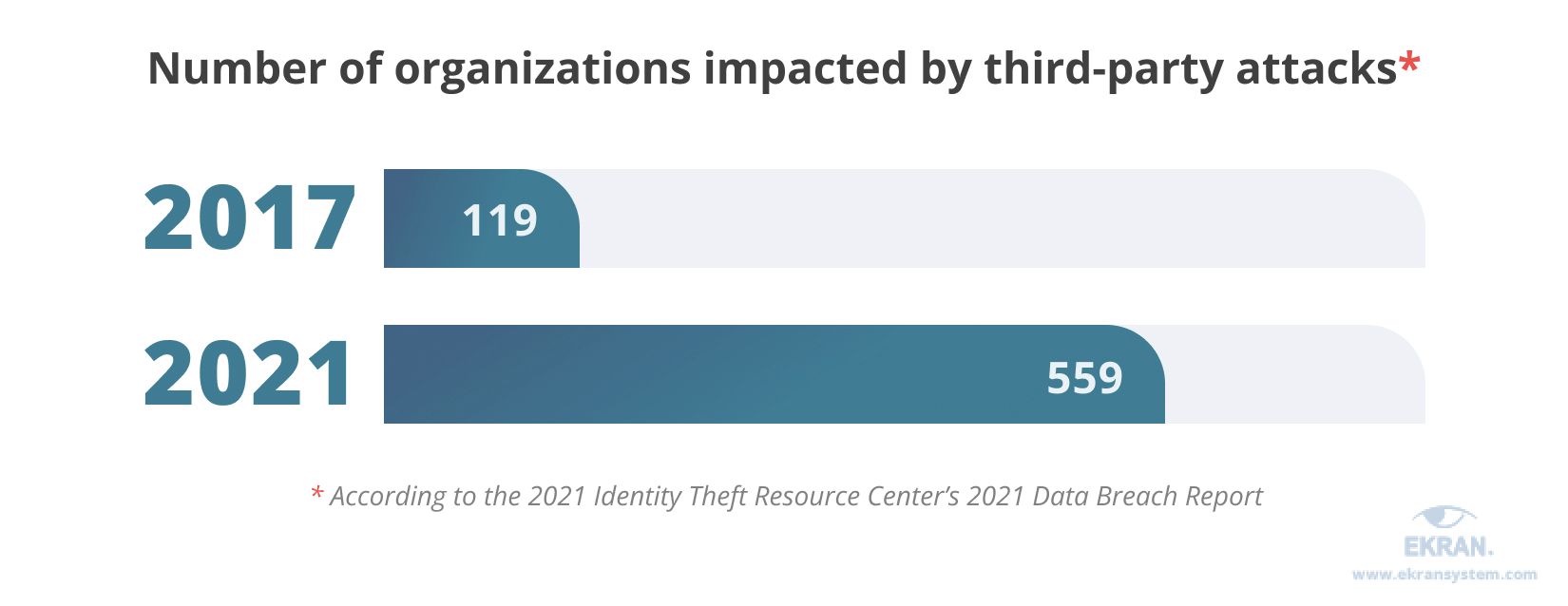
Monitor third-party access to your data
Third-party actors (vendors, partners, and contractors) are users with access to your organization’s resources and who can become easy victims in a supply chain attack. According to an ITRC report, the number of organizations impacted by third parties in supply chain attacks grew almost fivefold since 2017.
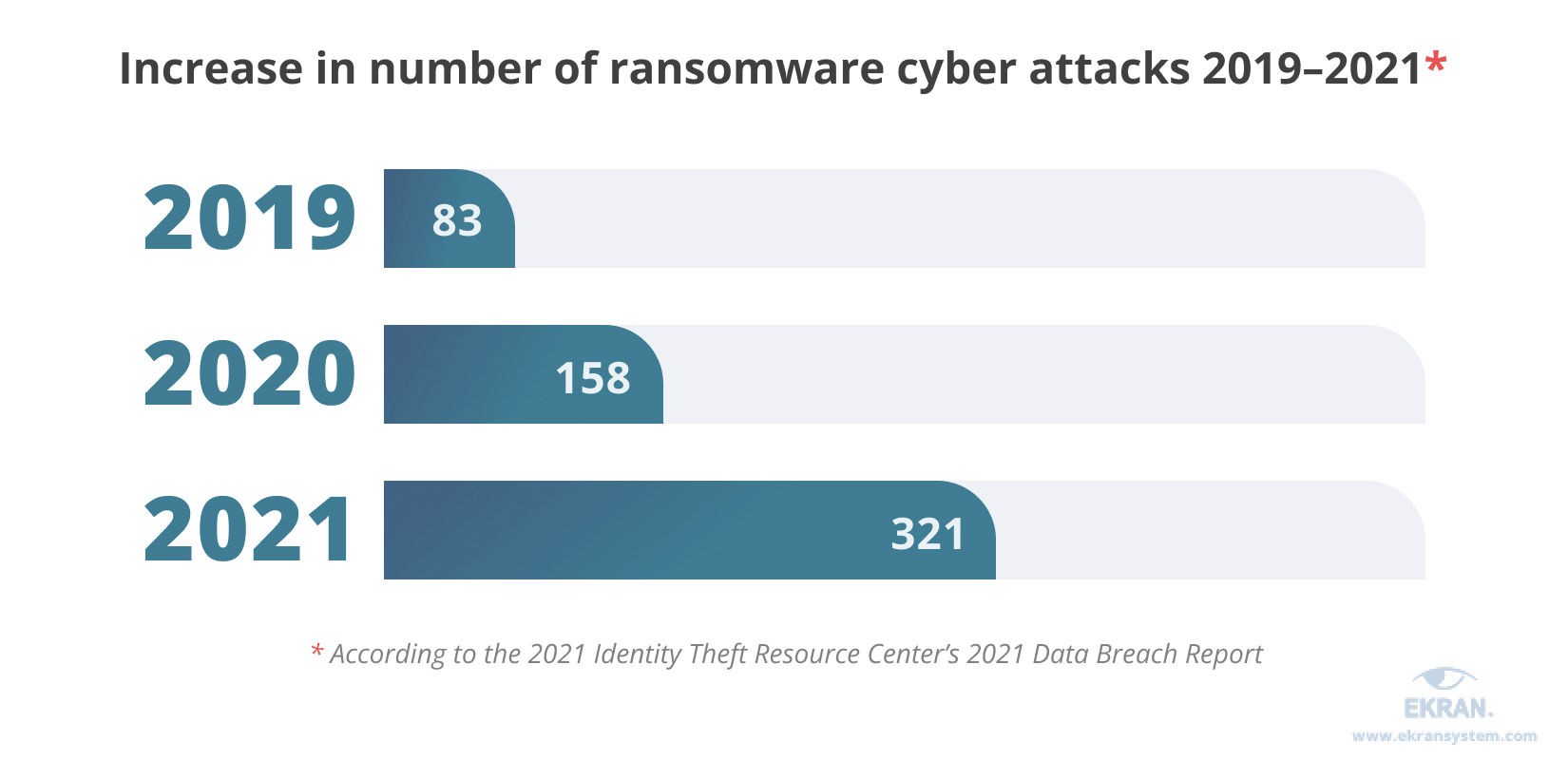
Back up your sensitive data
With the advent of ransomware, having full and current backups of all your data can be a lifesaver. Backing up data is one of the information security best practices that has gained increased relevance in recent years.
Ransomware takes second place among the top forms of cyber attacks in 2021 after phishing, and ransomware could easily surpass phishing in 2022 at the current growth rate; the ransomware attacks number has doubled in each of the past two years. In a ransomware attack, data is encrypted so a user can’t access it until they get a special key in exchange for paying a ransom.
Aside from ransomware, any kind of data loss can happen if your data is stored only in one place. Data loss can occur due to a breakdown of equipment, breach of cloud storage, deletion by mistake, and other factors.
Make sure that your backups are thoroughly protected, encrypted, and frequently updated. It’s also important to divide backup duties among several people to mitigate insider threats.
A strong backup strategy also means you are resilient to accidents. Don’t rely only on online backups, and don’t use the same passwords both for your production environment and for your backups. Instead, store your backups on offline endpoints and manage privileged access to them.
Build a robust cybersecurity policy and protected network
Form a hierarchical cybersecurity policy
First, a written policy serves as a formal guide to all cybersecurity measures used in your company. It allows your security specialists and employees to be on the same page and gives you a way to enforce rules that protect your data.
However, each department’s workflow is unique and can easily be disrupted by needless cybersecurity methods and measures.
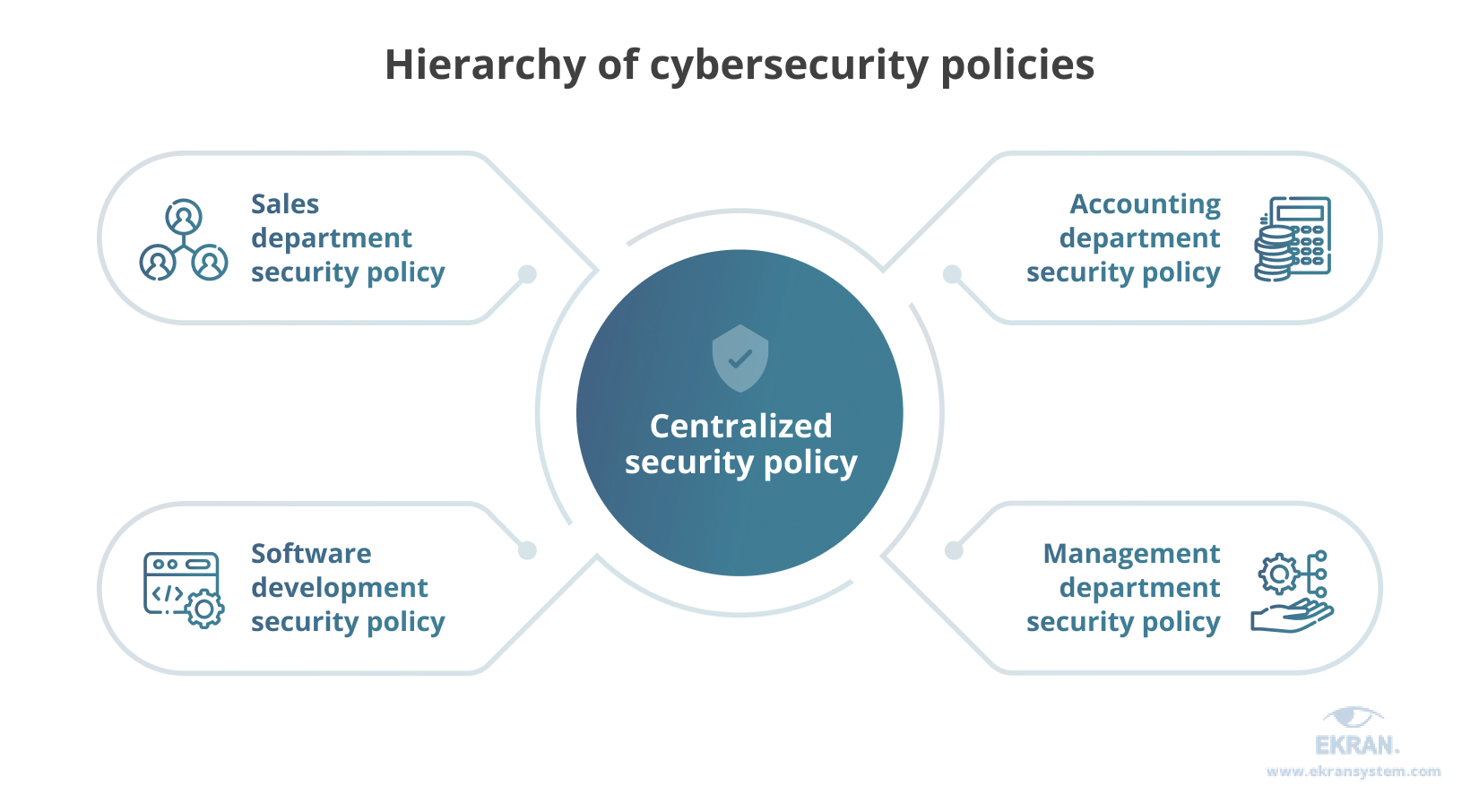
Second, while a centralized security policy can be beneficial as a basic guideline for the whole company, it shouldn’t cover every process in every department. Instead, allow your departments to create their security policies based on the central policy.
Manage IoT security and protect your corporate network
The most challenging thing about IoT devices is limiting their access to sensitive information. To manage these devices properly, consider implementing IoT network security best practices.
Markets and Markets predicts that the Internet of Things (IoT) market will grow to about $567 billion in 2027 from around $384 billion in 2021. But no matter how much we want to implement new technologies, security always comes first.
- Conduct penetration testing to understand the real risks for your devices to be broken into and plan your security strategy accordingly.
- Provide encryption for both data at rest and in transit (end-to-end encryption).
- Ensure proper authentication to allow only trusted connections to endpoints.
- Don’t use default and hardcoded credentials: commonly used passwords are easy to find on the internet.
- Purchase a secure and up-to-date router and enable the firewall.
- Develop a scalable security framework to support all IoT deployments.
- Consider implementing endpoint security solutions.
Conduct regular cybersecurity audits
Timely analysis of strange actions or movements of your employees, privileged users, or third-party vendors is key to dealing with sudden incidents promptly.
The quality of an audit depends on the completeness of the data collected in different ways or found in various sources: audit logs, session records, and metadata.
Organizations get up to 40% of data on user behavior from server logs according to a 2021 survey reported in the Insider Threat Report by Cybersecurity Insiders. They get another 30% of data via user and entity behavior analytics (UEBA).
Simplify your technological infrastructure
If your company’s cybersecurity infrastructure is aimed at decreasing the risk of data breaches, then it shouldn’t contain too many parts and be divided between different solutions.
Deploying lots of dedicated security tools has several downsides:
- It can be expensive to deploy and handle a lot of solutions in a complex infrastructure.
- Complex technological solutions can complicate proper security management.
- Resource-demanding software can slow down the work of other processes.
Some IT systems on the market may appear simple but complicated in reality. Consider one comprehensive solution that contains all the necessary functionality. This way, you’ll streamline and simplify your security infrastructure.
Protect access with efficient identity management
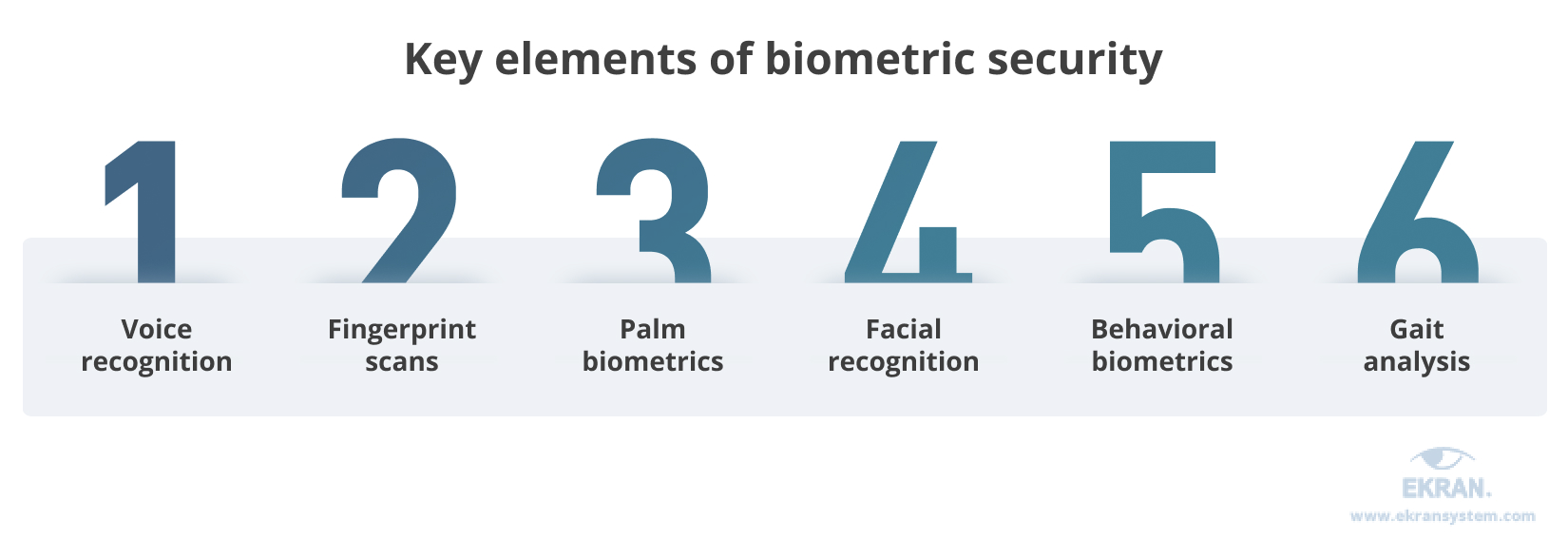
Employ biometric security
Biometrics ensure fast authentication, safe access management, and precise employee monitoring.
Voice recognition, fingerprint scans, palm, and behavioral biometrics, facial recognition, and gait analysis are perfect options to identify whether users are whom they claim to be. Verifying users’ identities before providing access to valuable assets is vital for your business.
Biometrics provides for more reliable authentication than passwords and SMS verification. That’s why biometrics has already become an essential part of multi-factor authentication.
However, authentication isn’t the only use for biometrics. Security officers benefit from a wide range of biometrics-driven tools that allow them to detect compromised privileged accounts in real-time.
Use multi-factor authentication
MFA helps you protect sensitive data by adding an extra layer of security, leaving malicious actors with almost no chance to log in as if they were you. Even if a malicious actor had your password, they would still need your second and maybe third “factor” of authentication, such as a security token, your mobile phone, your fingerprint, or your voice.
What are cybersecurity tools? (Free)
Small to medium-sized businesses often use a combination of free and paid open-source tools to improve their cyber security, tailoring the solution to protect their digital assets and networks according to their unique business operations needs.
Kali Linux is an open-source Debian-based Linux distribution offering a variety of free software, cyber security utilities, and penetration testing tools. It is one of the few hacking-focused Linux distributions that come pre-packaged with tools for reconnaissance and delivering payloads, as well as several other penetration-testing utilities.
Kali uses WSL (Windows Subsystem for Linux), which allows users to run Linux executable files directly from a Windows 10 system. The Kali OS supports embedded devices such as Raspberry Pi, Beaglebone, Odroid, HP & Samsung Chromebook as well as Android OS.
KeePass is a free and open-source password manager that securely stores passwords. These security tools enable users to have a single place for their unique passwords for websites, email accounts, web servers, or network login credentials.
KeePass works by storing passwords in a secure database, which unlock by entering a single master key. Database encryption is using the most secure encryption algorithms available: AES-256, ChaCha20, and Twofish. It encrypts the complete database, which means user names, notes, etc. are being encrypted along with the password fields.
Metasploit Framework is an exploitation and vulnerability validation tool that you can use offensively to test your systems for known and open vulnerabilities.
This open-source security tool is helping you to divide the penetration testing workflow into manageable sections, while you can also set up your workflows.
It is also a tool for auditing and network port scanning, which scans approximately 250 ports that are usually exposed to external services. An auto-exploitation feature works by cross-referencing open services, vulnerability references, and fingerprints to find corresponding exploits.
Nikto is a free and open-source web server scanner, which scans web servers for multiple vulnerabilities. The testing covers more than 6,700 potentially harmful files/programs and makes checks for outdated versions of over 1,250 servers. The web server scanner finds version-specific problems on over 270 servers. Users can also perform checks for server configuration issues such as the presence of multiple index files, and HTTP server options. This open-source security tool identifies installed web servers and software as well.
Nmap, Network Mapper, is used for penetration testing and security auditing. It uses NSE scripts to detect vulnerabilities, misconfigurations, and security issues concerning network services. Nmap maps network and ports before a security audit starts and then uses the scripts to detect any recognizable security problems. The app is fetching raw data and then determines a host type, type of operating system (OS), and all the hosts available within the network. Network administrators can use Nmap also for performing tasks around network inventory, service upgrade schedules, and monitoring uptime.
The open-source security tool runs on Linux, Windows, and Mac OS X. It is designed specifically for scanning large networks, but can be used to scan single hosts.
OpenVAS is an open-source and full-fledged vulnerability scanner, free for use. Users can perform unauthenticated testing and authenticated testing for various high-level and low-level Internet and industrial protocols. This tool also enables performance tweaking for large-scale scans. Users can perform any type of vulnerability test by taking advantage of its internal programming language.
OSSEC is an open-source, scalable, and multi-platform Host-based Intrusion Detection System (HIDS), whose creators want to keep free for the foreseeable future. Use OSSEC on-premise and in the cloud for server protection or as a log analysis tool that monitors and analyzes firewalls, IDSs, web servers, and authentication logs.
OSSEC can withstand cyber-attacks and system changes in real-time utilizing firewall policies, and integration with third parties such as CDNs, and support portals. The application features self-healing capabilities and provides application and system-level auditing for compliance with many common standards such as PCI-DSS and CIS.
Security Onion is a Debian-based Linux distribution for detecting threats, enterprise security monitoring, and log management. It incorporates security tools such as Elasticsearch, Logstash, Kibana, Snort, Suricata, Zeek, OSSEC, Wazuh, Sguil,
Squirt, NetworkMiner, and others to protect an organization against cyber threats.
It is an all-in-one open source security solution that provides users with various tools to detect threats and monitor their systems.
VeraCrypt is a security tool for disk encryption. It runs on Windows, Mac OSX, and Linux and creates a virtual encrypted disk within a file before mounting it as a real disk.
This tool encrypts an entire partition (file storage drive) or storage devices such as a USB flash drive or hard drive before dumping it into the cloud or elsewhere.
Users can also pre-boot authentication by encrypting a partition or drive where the Windows OS is installed. VeraCrypt encrypts in real-time and supports hidden drives and hidden operating systems on a machine.
Wireshark is a free and open-source tool for network protocol analysis. This cybersecurity tool enables security professionals to observe the network at a microscopic level by viewing the traffic, dumping specific packets, checking the packet format, and finding network issues this way.
It is available for multiple platforms including Runs on Windows, Linux, macOS, Solaris, FreeBSD, and NetBSD allowing for deep inspection of hundreds of protocols. Wireshark supports live capture and offline analysis of data and offers decryption for multiple protocols such as for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2.

Cybersecurity and Ethical hacking
Ethical hacking is the authorized practice of examining a system to pinpoint its weak points, which can be exploited by malicious hackers. An ethical hacker is a type of security professional who, unlike a malicious hacker, does not have malicious intent. Instead, an ethical hacker seeks to protect the system and will alert anyone that may be affected or at risk.
When sensitive customer data is exposed to potential malicious misuse, a company should engage an ethical hacker to prevent any security breach. If such a breach occurs, the ethical hacker will ensure customer and client information is protected and recover it when necessary.
Cybersecurity and Digital forensics
cybersecurity is the practice of protecting computer data from unauthorized access, use, or destruction. Information security experts typically implement three types of controls to safeguard information systems: technical, physical, and administrative. The computer forensics team works to identify the hack, understand the source, and recover compromised data. The two fields are highly reliant on one another to maintain ongoing network security for organizations across numerous industries and sectors.
what is cybersecurity governance?
Cybersecurity governance is a critically important part of managing security and risk in organizations large and small. As a responsibility of boards and executive leaders to enforce, cybersecurity governance ensures that a company’s cybersecurity model and program align with business objectives, complies with government or industry regulations, and achieves the goals that leadership has set out for managing security and risk.
what is a cybersecurity audit?
A cyber security audit is a systematic and independent review of an organization’s cyber security. Audits ensure that the proper security controls, policies, and procedures are in place and working effectively. The end result is a report which details any high-risk security issues and how they can be resolved.
what is the cybersecurity act?
The Cybersecurity Act strengthens the EU Agency for cybersecurity (ENISA) and establishes a cybersecurity certification framework for products and services.
ENISA, the EU Agency for cybersecurity, will have a key role in setting up and maintaining the European cybersecurity certification framework by preparing the technical ground for specific certification schemes.
ENISA is mandated to increase operational cooperation at the EU level, helping the EU Member States who wish to request it to handle their cybersecurity incidents, and supporting the coordination of the EU in case of large-scale cross-border cyberattacks and crises.
A European cybersecurity certification framework
The EU Cybersecurity Act introduces an EU-wide cybersecurity certification framework for ICT products, services, and processes. Companies doing business in the EU will benefit from having to certify their ICT products, processes, and services only once and see their certificates recognized across the European Union.
More on the certification framework
when is cybersecurity awareness month?
October: Cybersecurity Awareness Month
Every year since 2003 October has been recognized as Cyber Security Awareness Month (CSAM). This effort was brought to life through a collaboration between the U.S. Department of Homeland Security and the National Cyber Security Alliance. CSAM was created to ensure that every individual stays safe and secure online.
what is the future of cybersecurity?
Cybersecurity has existed since the creation of the first computer virus in 1971. That was the “creeper” virus, a harmless application designed to replicate and move from computer to computer.
Cyberthreats have grown in scale and complexity and the tools available to detect and prevent threats have likewise improved. Machine learning and AI are being used by both sides to continue this game of cat-and-mouse. Quantum computing will be next, exponentially elevating the capabilities of an attacker and a defender. So the cat and the mouse will keep getting better and faster, but the overall game isn’t going to change too much.
The future of cybersecurity will be challenging, but with the collaboration of government agencies, educational institutions, and innovative technology companies, we can elevate our collective efforts to match the growing threat head-on. We must rise as a whole community to meet this challenge.
Resources
https://www.ibm.com/topics/cybersecurity
https://www.itgovernance.co.uk/what-is-cybersecurity
https://www.kaspersky.com/resource-center/definitions/what-is-cyber-security
https://onlinedegrees.unr.edu/ms-in-cybersecurity/resources/why-is-cybersecurity-important/
https://www.ekransystem.com/en/blog/best-cyber-security-practices
https://illinois.touro.edu/news/top-10-cybersecurity-best-practices-for-your-business.php
25 Cyber Security Terms That Everyone Who Uses A Computer Should Know
https://www.cybintsolutions.com/20-cyber-security-terms-that-you-should-know/



0 Comments