90% of passwords can be cracked in less than six hours
Despite warnings, the migration to two-factor authentication systems has been slow, leaving many accounts vulnerable. Now, as consumers and companies have become aware of the dangers of basic password protection, the demand for stronger 2FA/MFA systems is expected to increase.
What is the best description of two-factor authentication?
Multifactor authentication (MFA), also known as two-factor authentication, is a security measure that requires users to prove their identity using two different methods. Two-factor authentication can be implemented through numeric codes sent through text messages or generated by an application on your smartphone, or by accessing a unique identifier tied to a physical device like a USB key or a dongle on your keychain.
Why use 2FA (2-factor authentication)?
Two-factor authentication (2FA) is one of the most effective—and most important—security measures that anyone can apply to their online accounts. It’s a way for accounts to verify your identity by requiring not only a password but also something only you have on hand, such as your phone, or a special code that could only be generated by an app installed on that phone. By requiring two types of identification to authorize logins, 2FA can quickly neutralize the risks associated with compromised passwords or even phishing attacks.
The National Cyber Security Centre suggests using two-factor authentication (2FA) and UK regulation governs strong customer authentication (SCA) in the finance sector. Meanwhile, Twitter now allows users to use security keys as their only 2FA method.
How two-factor authentication works?
Different 2FA methods use varying processes, but they all rely on the same underlying workflow.
Typically, a 2FA transaction happens like this:
- The user logs in to the website or service with their username and password.
- The password is validated by an authentication server, and if correct, the user becomes eligible for the second factor.
- The authentication server sends a unique code to the user’s second-factor device.
- The user confirms their identity by approving the additional authentication from their second-factor device.
While the basic processes behind multi-factor authentication are generally the same across providers, there are many different ways to implement it, and not all methods are created equal. Let’s dive into the various types of 2FA.
What are the types of 2FA?
There are several types of 2FA available, all of them relying on the different forms of factors we’ve listed above.
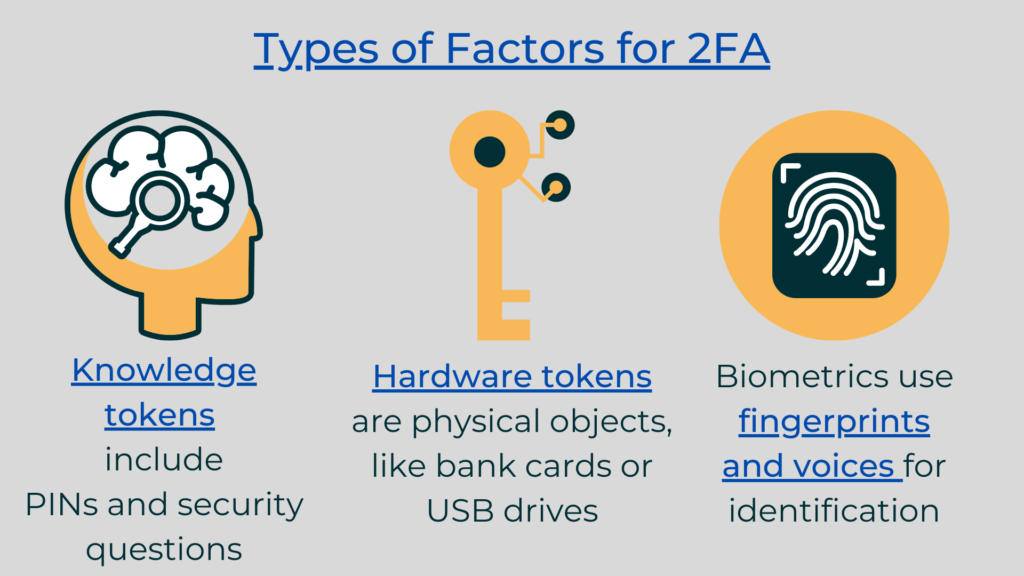
- Hardware tokens: This type of 2FA requires users to possess a type of physical token, such as a USB token, that they must insert in their device before logging on. Some hardware tokens display a digital code that users must enter.
- SMS and voice 2FA: You’ll receive either a text or voice message giving you a code that you must then enter to access a site or account.
- Software tokens for 2FA: These tokens are apps that you download. Any site that features 2FA, will then send a code to the app that you enter before logging on.
- Push notifications for 2FA: You’ll download a push notification app to your phone. When you enter your login credentials to access a website, a push notification is sent to your smartphone. A message will then appear on your phone requesting that you approve your log-in attempt with a tap.
- Biometrics: To log onto a site, you’ll first have to verify it’s you through something physical about yourself. Most commonly, this means using a fingerprint scanner.
- Location: If your account was created and registered in one state, and suddenly a log-in is attempted in a different location, it may trigger a location factor. These factors will alert you when a log-in is attempted on a new device and send you a code to enter to verify your identity.
How secure is 2FA?
A harsh reality: No security protocol is failsafe. Cybercriminals may still access your account even if you enable two-factor authentication (2FA). For example, account recovery may allow hackers to bypass 2FA, resetting your password via email and gaining access to your accounts. However, precautions like adding a second layer of security are better than taking no action at all.
What are the benefits of two-factor authentication for business?
- Increases Security
By requiring users to provide multiple credentials prior to accessing accounts, hackers are prevented from using stolen passwords, devices, or other individual pieces of information to enter your network.
- Reduces Risk from Compromised Passwords
While passwords are the most common form of authentication, they are the least secure. People may reuse or share passwords, which can also be stolen or guessed, leading to exposure for account holders and system administrators.
A 2021 Verizon Data Breach Investigations Report found that 61 percent of breaches in 2020 were executed using unauthorized credentials.
- Customizable Security Solution
Each authentication factor offers multiple options, providing enterprises with the ability to customize the user experience to meet their needs. For example, users might have access to fingerprint scanners on their smartphones, but not retinal or voice recognition scanners. Two factors may be sufficient for some use cases, while others may require all three authentication factors.
- Compatible with Single Sign-On (SSO)
MFA can be embedded into applications and integrated with single sign-on. Users no longer have to create multiple unique passwords or make the risky choice of reusing the same password for different applications when logging in. Together with SSO, MFA reduces friction while verifying the user’s identity, which saves time and improves productivity.
- Scalable for Changing User Bases
Multi-factor authentication easily adapts to your business needs. MFA can be set up for all users, including employees, customers and partners. Single sign-on combined with MFA eliminates the need for multiple passwords, streamlines the login process, improves the user experience, and reduces the number of calls to IT departments for password assistance.
- Regulatory Compliance
There may be industry or geographical regulations requiring MFA. For example, Payment Card Industry Data Security Standard (PCI-DSS) requires that MFA be implemented in some situations to prevent unauthorized users from accessing payment processing systems. It also helps meet strong customer authentication requirements dictated by Payments Service Directive 2 (PSD2) in the EU. In addition, MFA helps healthcare providers comply with the Health Insurance Portability and Accountability Act (HIPAA).
- Enables Enterprise Mobility
The pandemic made remote work options necessary for many organizations and sped up the digital transformation. Allowing employees to use mobile devices to easily and securely access the resources they need increases productivity. Using MFA to log into business applications, especially when integrated with SSO, provides the flexibility and 24/7 access employees need while keeping networks and data protected.
- Adaptable for Different Use Cases
Some situations call for greater security, like conducting high-value transactions and accessing sensitive data from unknown networks and devices. Adaptive MFA uses contextual and behavioral data such as geolocation, IP address, and time since the last authentication to assess risk. If the IP address is considered risky (e.g., coffee shop or anonymous network) or other red flags are noted, authentication factors can be added as needed to gain a higher level of assurance about a user’s identity.
Conclusion
Multiple-factor authentication is the most effective step you can take to prevent security breaches. Governments and corporations are increasingly interested in cybersecurity and banks, the military, and government agencies are investing in better authentication solutions. Multi-factor authentication is the first line of defense against unauthorized data breaches.
If you are interested please read the following content to get a deeper knowledge.
Read “8 Benefits of Multi-Factor Authentication (MFA)” by pingidentity.com here
Read a Deep dive about Two Factor Auth (2FA) from Brain Station here
UK National Cyber Security Centre Guide for Setting up 2-Step Verification
Uk Government Digital Services Guide on Using authenticators to protect an online service
Photo by Philipp Katzenberger on Unsplash



0 Comments